Synology RT1900ac Review – Intelligent DNS-based Web-filter
Under Parental Control, there is a web-filter feature that blocks access to websites base on the their content categories (i.e. adult, gambling, drugs). For each of the device, you can choose either basic, protected or custom filter. Only one custom filter can be configured.
| Other parts of the Synology RT1900ac Review | |
|---|---|
| 1 | Introduction |
| 2 | Initial Setup and Synology Router Manager |
| 2.1 | Intelligent DNS-based Web-filter |
| 2.2 | Using as NAS |
| 3 | Speed Test |
Configuring the Web-Filter
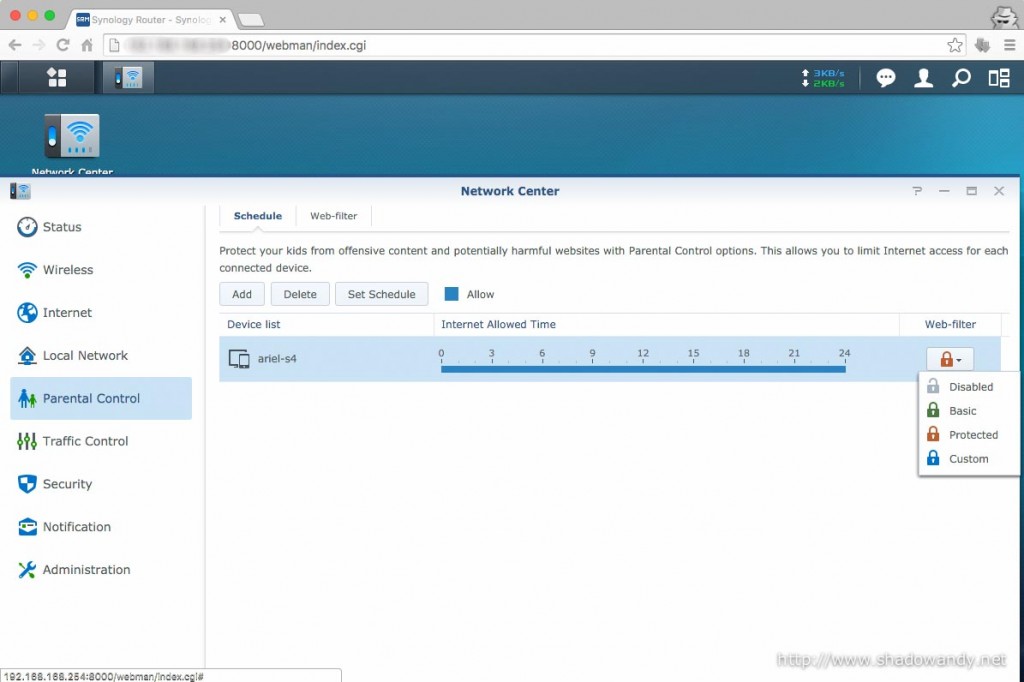
The Web-filter feature can be found under the Parental Control section. In order to use the web-filter, the device has to be added to the list. Once it has been added to the list, the schedule for Internet allowed time also kicks in. Under the web-filter column on the right, you can choose the level of filter (basic, protected or custom) to be applied to the selected device.
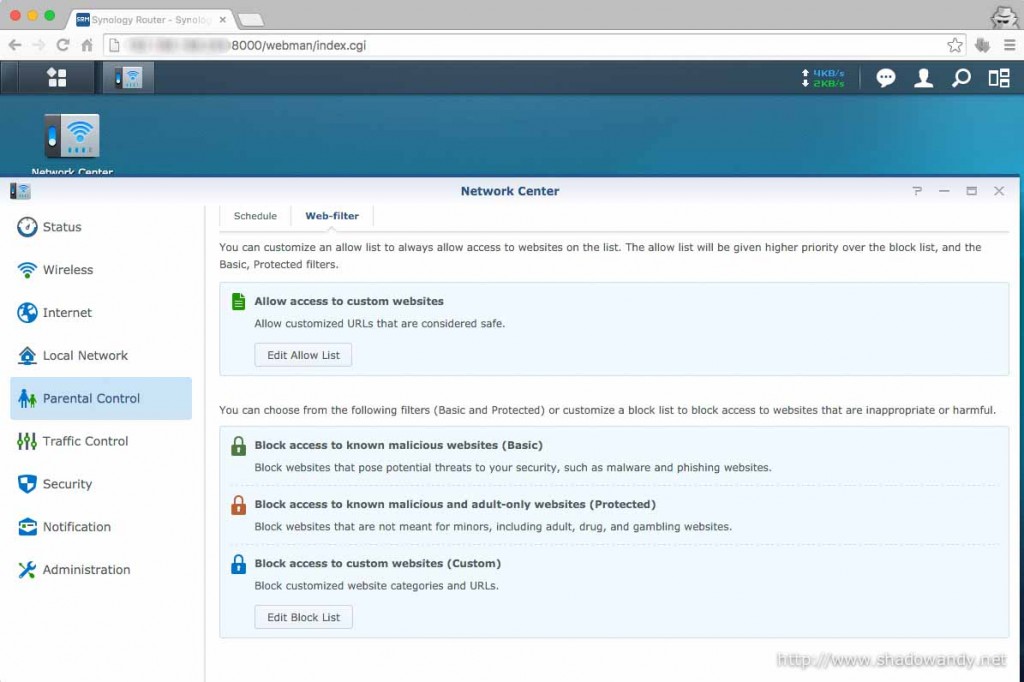
Under the settings for Web-filter, you can whitelist websites, blacklist websites on top of the existing content categories or customise your own filter by choosing from the available content categories.
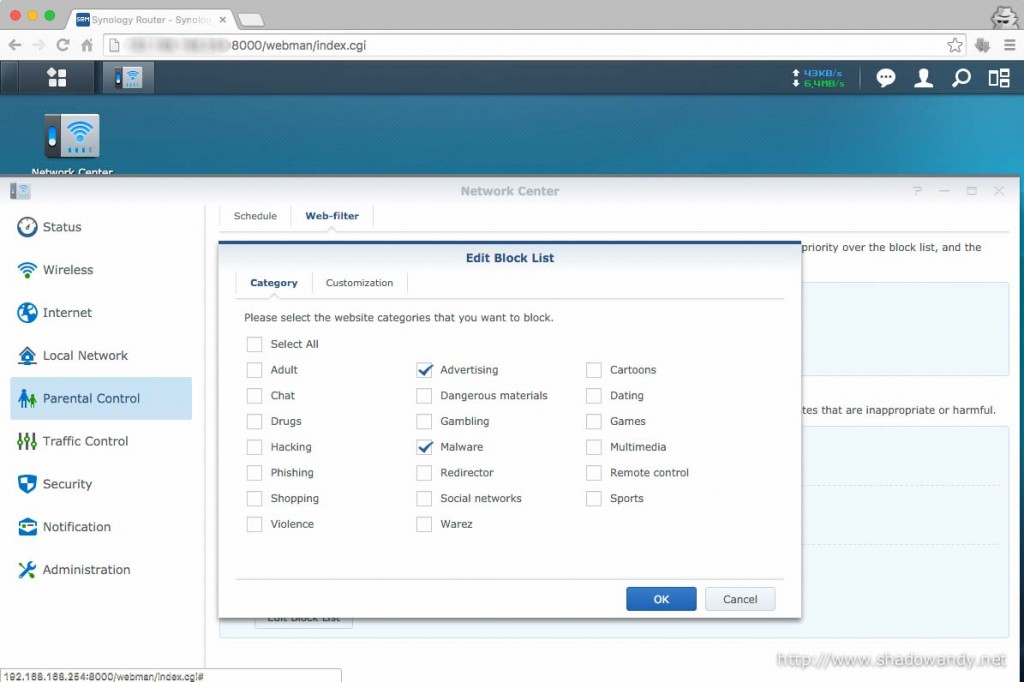
The content categories are quite extensive. I am curious if the websites under each categories are updated periodically.
Accessing blocked websites

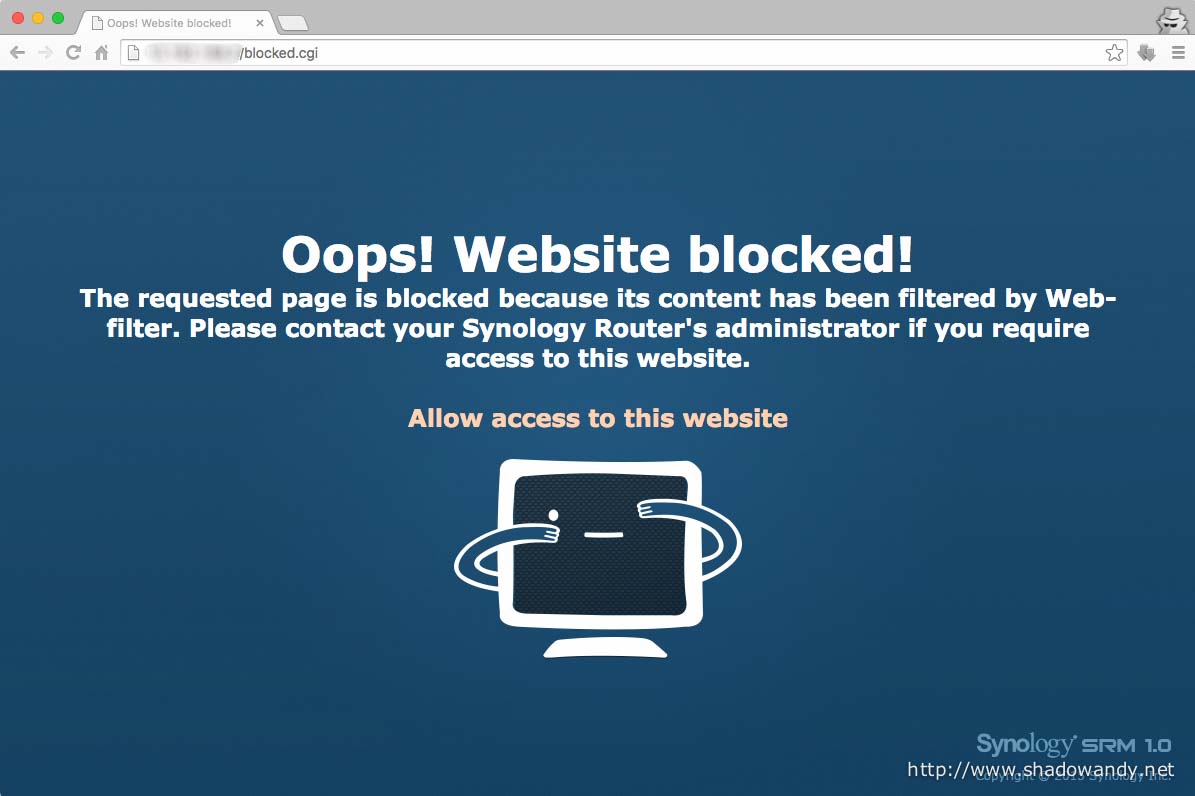
If one try to access a website that is on the blocked list, they will see the above “Oops! Website blocked” page. From this page, the admin have the option to whitelist the page.
Behind the scene
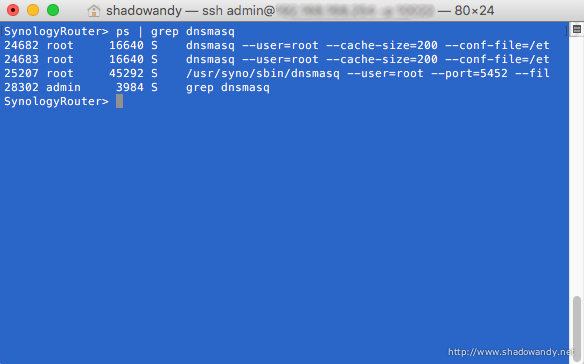
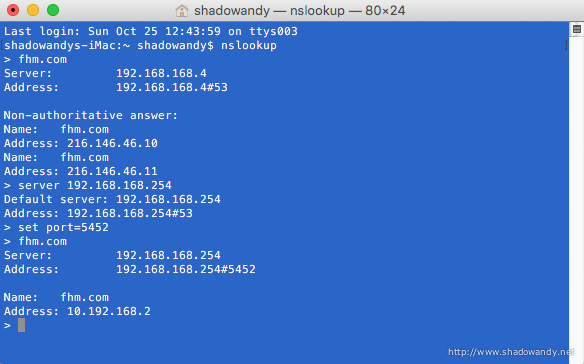
Behind the entire web-filter magic is the work of dnsmasq and iptables. A dnsmasq instance that resolves blocked hostnames/ website to an IP address (in this case is 10.192.168.2) that hosts the “Oops! Website blocked” page.
Next is the clever use of iptables to route DNS requests from the web-filtered devices (based on their MAC address) to that dnsmasq instance. The next set of iptables rules directs devices to a http instance on the Synology RT1900ac hosting the “Oops! Website blocked” page.
1 2 3 4 5 6 7 8 | -A URL_BLOCKER -p udp -m udp --dport 53 -m mac --mac-source C8:2A:14:5A:3C:12 -j REDIRECT --to-ports 5452 -A URL_BLOCKER -p tcp -m tcp --dport 53 -m mac --mac-source C8:2A:14:5A:3C:12 -j REDIRECT --to-ports 5452 -A URL_BLOCKER -p udp -m udp --dport 53 -m mac --mac-source 5C:F8:A1:5A:39:CA -j REDIRECT --to-ports 5452 -A URL_BLOCKER -p tcp -m tcp --dport 53 -m mac --mac-source 5C:F8:A1:5A:39:CA -j REDIRECT --to-ports 5452 -A URL_BLOCKER -s 192.168.128.0/24 -d 10.192.168.2/32 -p tcp -m tcp --dport 80 -j DNAT --to-destination 192.168.128.254:5010 -A URL_BLOCKER -s 192.168.128.0/24 -d 10.192.168.2/32 -p tcp -m tcp --dport 443 -j DNAT --to-destination 192.168.128.254:5011 -A URL_BLOCKER -s 192.168.129.0/24 -d 10.192.168.2/32 -p tcp -m tcp --dport 80 -j DNAT --to-destination 192.168.129.1:5010 -A URL_BLOCKER -s 192.168.129.0/24 -d 10.192.168.2/32 -p tcp -m tcp --dport 443 -j DNAT --to-destination 192.168.129.1:5011 |
So meaning to say, changing DNS server on the web-filtered device won’t bypass the web-filtering feature. Using a VPN will help as long as the DNS traffic doesn’t go through the iptables (on the Synology RT1900ac). Lastly, using the local hosts file should work too.